How is the Canadian market embracing Cyber Security?
As a big, economically diverse nation, Canada is experiencing various degrees of the effects of tremendous technology changes. As complex as the economy is, there is a very high rate of technology adoption in various sectors, and there is the need to protect it. One of the predecessors for introducing technology changes and enhancements in the Canadian market is the finance and insurance sector that uses this technology to stay competitive and meet the ever-increasing demands of digital services customers, and today than ever it’s very necessary to protect all your assets and thus multiple industries are taking rigorous steps to protect their assets and welcoming all measures to ensure it.
Core functions
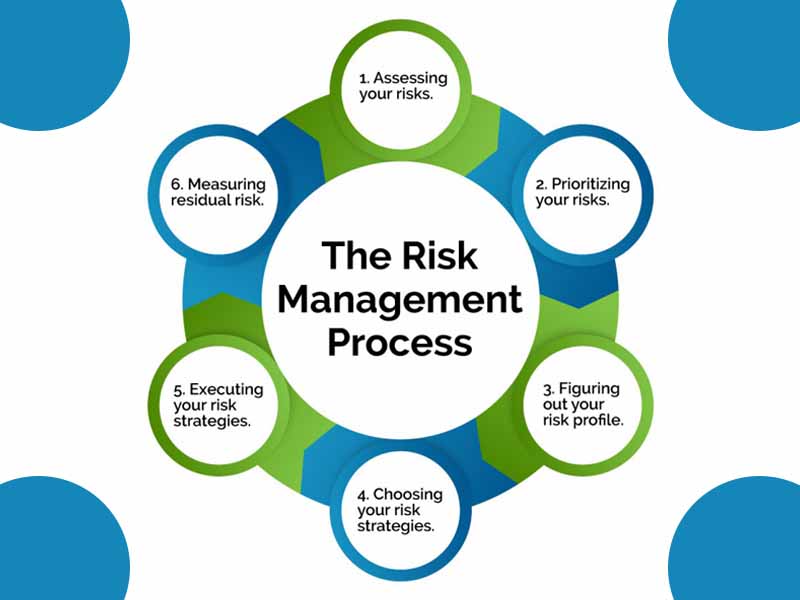
Identification is the first core function of CyberSecurity is to identify the organization’s cyber risk, which is the amount of risk posed by the organization’s activities, connections, and operational procedures. Vulnerability assessment; proactive cyber intelligence; governance, risk & compliance; asset management is a few examples of the solutions.
Protection is to ensure that the organization has the appropriate safeguards or controls in place to mitigate the various types of threats. This is the first line of defense and threat prevention; access control; data security; patch management are a few solutions.
Detection helps to monitor deviations from the normal state of activity. Continuous (24/7) monitoring; anomaly & threat detection; user & application awareness; predictive analytics are the measures that can be taken.
Level of responsiveness is an important factor that an organization should prepare for an incident, including knowing how the organization will respond if an incident occurs.
An organization can use incident response; malware analysis; forensic remediation to increase the response.
Recovery includes appropriate processes and procedures for how one intends to restore confidence in the recovered systems and data, continuity of operations; disaster recovery; threat mitigation should be used for recovery.



Cybersecurity Services
IT Risk Management: Our IT Risk Management services help organizations tackle many security challenges they face on a daily basis — supporting risk-based decisions and improved cybersecurity, reducing costs related to managing security risk, and improving their overall cybersecurity posture.
Vendor Risk Management: Organizations that rely heavily on vendors but don’t have sufficient visibility into their vendor networks are exposing themselves to high risks. A strong Vendor Risk Management (VRM) program helps companies anticipate inherent risks rather than simply reacting to adverse situations and incidents after they occur.
Compliance Management: The rising incidence of fraud, corruption, and bribery, as well as legal, compliance, and ethical violations have resulted in greater liabilities and penalties for organizations than ever before. An effective corporate compliance program is no longer just an option— it is a necessity. The executive leadership and three lines of defense must be able to work together towards a common goal of sustaining compliance and trust with customers and stakeholders.
Threat & Vulnerability Management: Vulnerability management is the process in which vulnerabilities in IT are identified and the risks of these vulnerabilities are evaluated. Organizations that rely heavily on vendors but don’t have sufficient visibility into their vendor networks are exposing themselves to high risks. A strong Vendor Risk Management (VRM) program helps companies anticipate inherent risks rather than simply reacting to adverse situations and incidents after they occur.
Compliance Management: The rising incidence of fraud, corruption, and bribery, as well as legal, compliance, and ethical violations have resulted in greater liabilities and penalties for organizations than ever before. An effective corporate compliance program is no longer just an option— it is a necessity. The executive leadership and three lines of defense must be able to work together towards a common goal of sustaining compliance and trust with customers and stakeholders.
Threat & Vulnerability Management: Vulnerability management is the process in which vulnerabilities in IT are identified and the risks of these vulnerabilities are evaluated.
